In the quiet dawn of May 7, 2021, a pivotal artery of the American energy infrastructure came under a malicious digital siege. The Colonial Pipeline - a vital oil pipeline system stretching from Houston, Texas, and coursing its way through the southeastern United States - suddenly found itself in the crosshairs of a devastating cyberattack.
The reverberations of this attack rippled through the nation, creating not just small waves but a seismic disruption in the realms of fuel distribution, energy security, and the safeguarding of critical infrastructure. Join us as we delve into the heart of the Colonial Pipeline cyberattack, peeling back the layers to uncover the impact of the attack and the broader reverberations it created in the realms of cybersecurity and the resilience of our energy systems.
The Colonial Pipeline stands as a critical lifeline for the southeastern United States. As a major company, responsible for ferrying 45% of the fuel consumed on the East Coast, it spans over an impressive 5,500 miles. Serving as the primary channel for the transportation of gasoline, diesel, and jet fuel, it begins its journey from the bustling refining hub in Houston, Texas and extends to pivotal distribution centres in the southeastern United States. This network of pipes fuels not just the Southeastern states, such as Georgia, South Carolina, North Carolina, and Virginia, but also states as far north as New Jersey.

Shown above is a map detailing the extent of the pipeline distribution in the southeastern region of the United States, specifically, the Colonial Pipeline distribution and refineries.
Initial Intrusion
The cyberattack on the Colonial Pipeline began when the attackers gained unauthorized access to the pipeline's computer systems. A vulnerable remote access system through an exposed password on a VPN is the most likely attack vector.
A vast majority of enterprises use a VPN service to secure and encrypt remote access to their network, but any employee reusing enterprise credentials on another site could compromise this network.
The initial attack vector has not yet been established, and although we suspect it to be a compromised password on a VPN; it may also have been an old, unpatched vulnerability on their system, a spear-phishing email that targeted an employee, the use of leaked or purchased access credentials from a myriad of sources, or one of many other tactics employed by cybercriminals to gain unauthorized access to a company's network.
Timeline
May 6, 2021
- Initial intrusion and data theft.
May 7, 2021
Ransomware attack begins.
Colonial Pipeline becomes aware of the attack.
Federal authorities are notified of the attack.
The Colonial Pipeline network is taken offline to prevent further intrusion and damage.
A ransom of $4.4 million (75 BTC) is paid to the hackers.
May 9, 2021
- Joe Biden makes an emergency declaration.
May 12, 2021
- Colonial Pipeline resumes normal operations.
June 7, 2021
- The Department of Justice recovers $2.3 million (63.7 BTC) from the attackers.
Ransomware Deployment
Once the hackers gained access to the network, they started to deploy ransomware that encrypted all the corporate files.
It is to be noted that the ransomware had targeted the business front of Colonial Pipelines but it eventually did do some damage to their operational systems. This means the purpose of the ransomware was to make money rather than to cause disruptions in the operation of the pipeline.
As the files across the corporate network were encrypted, Colonial Pipelines decided to shut down certain sections of their operational apparatus to prevent further damage, but this created ripple effects in the market.
On May 6th, the hackers had stolen 100 GB of data before encrypting systems and demanding a ransom be paid.
As per IBM X-Force reports, the malware - upon activation - performs data exfiltration, encrypts system data using the Salsa20 and the RSA-1024 encryption protocols, and then executes an encoded PowerShell command to remove volume shadow copies.
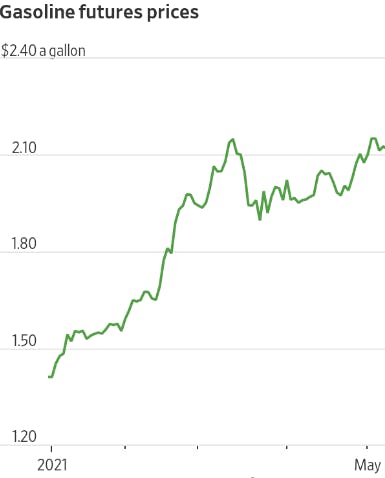
The shutdown of certain sections of the pipeline had far-reaching consequences as the price of gasoline skyrocketed across the southeastern region - causing panic buying and further increasing gas prices. The cyberattack also prompted a shortage of jet fuel, causing minor disruption in Atlanta and Nashville.
Below is a graph of the price fluctuation during the shutdown.
Response and Recovery
The goal of the attacker was to get paid a ransom, which Colonial Pipeline did, by paying a sum of $4.4 million (75 BTC). The main reason the ransom was paid in Bitcoins is that cryptocurrency payments are assumed to be untraceable and that they cannot be recovered after the transaction.
U.S. Department of Justice's Ransomware and Digital Extortion Task Force traced the ransom paid by Colonial Pipeline and recovered a significant part of the ransom - $2.3 million (63.7 BTC).
To recover the money, the Department of Justice took legal action against an exchange (or custodial wallet) that had its servers in Northern California. The DoJ thus obtained the private key to the wallet the hackers had used to receive the ransom.
Who Was Responsible For The Attack?
The Colonial Pipeline attackers were identified as a hacking group by the name of DarkSide. The group's initial activities were reported around August 2020, and it is said to be operating out of Eastern Europe or Russia, where the group had undertaken a malicious campaign of infecting victims with ransomware. To date, there is no confirmed link to any state-sponsored activity.
One of the strategies employed by DarkSide is Ransomware-as-a-Service (RaaS). Through RaaS, DarkSide offers its ransomware capabilities to various threat actors. This enables these threat actors to employ ransomware without having to develop it themselves, thereby streamlining their attacks on potential targets. Typically, such services are accessible through less conventional platforms (like the dark web).
DarkSide has already created a leak website that is used for double-extortion campaigns, where the targeted companies are not only locked out of their systems but also have their information stolen.
Aftermath
In the aftermath of the Colonial Pipeline ransomware attack, industry and government agencies set out to find ways to mitigate or prevent similar incidents from happening in the future.
In attacks like the one that impacted Colonial Pipeline, the primary attack vector typically stems from a vulnerable component lurking within an organization's infrastructure. Identifying and addressing this vulnerability can prove challenging for large organizations, especially when it involves understanding the contents of all in-use applications and identifying potential software dependencies that might include known vulnerabilities. Additionally, there is a risk of a zero-day attack on a software component for which a patch isn't available.
At times the vulnerabilities can also be due to human errors. Phishing attacks are often used against unsuspecting employees, and some employees use weak/default passwords or reuse passwords, which is what we suspect happened in the case of the Colonial Pipeline attack.
The US government - specifically, the Department of Homeland Security (DHS) and the FBI - responded by issuing advisories and guidance to companies responsible for critical infrastructure.
The cyberattack on Colonial Pipeline brought forth a stark realization of the vulnerabilities within essential infrastructure sectors, including energy, water, and transportation. It prompted a comprehensive review of security measures and raised significant concerns regarding the potential for future attacks on critical services.
The Colonial Pipeline attack offers valuable insights into the repercussions of cyberattacks on vital public infrastructure. It underscores the urgent need for enhanced security practices, the exchange of critical information, and global collaboration to effectively prevent and mitigate such incidents.
Additionally, it emphasizes the importance of organizations and governments proactively strengthening their cybersecurity defences.
References:


